Scripting the crime and identifying the target
You’ll probably have noticed that this week, the Oscars took place. In the end, I chose sleep over staying up to watch the ceremony (my tolerance for sleep deprivation has, er, “decreased in inverse proportion” to my age). But as the fallout settles, I’ve been thinking about the movies.
Take the idea of a film script; say it’s a film about environmental crime. (The message flashes up at the beginning: “this is a true story…”) This film script has many scenes, over the course of which, a story develops. Then there’s the cast – all of whom have different roles with varying depths of involvement. Some only have bit parts – but their appearance might nevertheless be central to the plot – and then there are some that are present throughout.
The location of each scene depends on the characters’ particular activities (the forest, the tannery, the border crossing). The actors need “props” to carry out their roles, ranging from traditional traps to firearms, helicopters with obscured registrations and satellite phones.
With all this activity, we need to remember what binds the script and story together, changing hands on its complicated and covert journey from origin to destination. Whether it’s rhino horn, elephant ivory, tiger skin…I’ve realised that my favourite character would already be dead before the film starts.
This isn’t just a metaphor, but another way of looking at crime. For several years now, criminologists like Derek Cornish have been developing “crime scripts” which identify and isolate what criminal actors require to perfectly execute their parts –in terms of both tools and (spoken like a true thespian) “motivation”.
Each activity is broken down into “acts” like in a play or the scenes in our film. Reading through, you get a sequential chain of criminal decisions and behaviours, along with what is required to undertake each act successfully. So if the poaching of a tiger is one act or scene, to “perform” the act successfully, preparation activities are inherent: poachers gather local intelligence about tiger sightings; they identify the water holes the tiger has frequented; they block paths to all water holes but one, then poison water in the remaining hole, and so on.
So when you have your entire crime script – from poaching to end market – and the culmination of all of these acts, preparation activities and facilitators, you can identify intervention points throughout and say, “there’s a point where we can make a change”; and so, we hope, re-write the outcome of the film.
It might not be a typical “happy ending” – but at least one in which criminals are identified, investigated and prosecuted. Then, there will be other interventions that can deter – or even recruit into conservation.
At EIA, we believe it’s fundamental that the complexity of criminal networks is recognised – along with their ability to react, mutate and recover from enforcement efforts. Ultimately, crime is great at survival. Enforcement needs to be sensitive to this reality. Enforcement shouldn’t, for example, be “scripted” to the extent that law enforcement actions are announced publicly, in advance of being carried out! 1
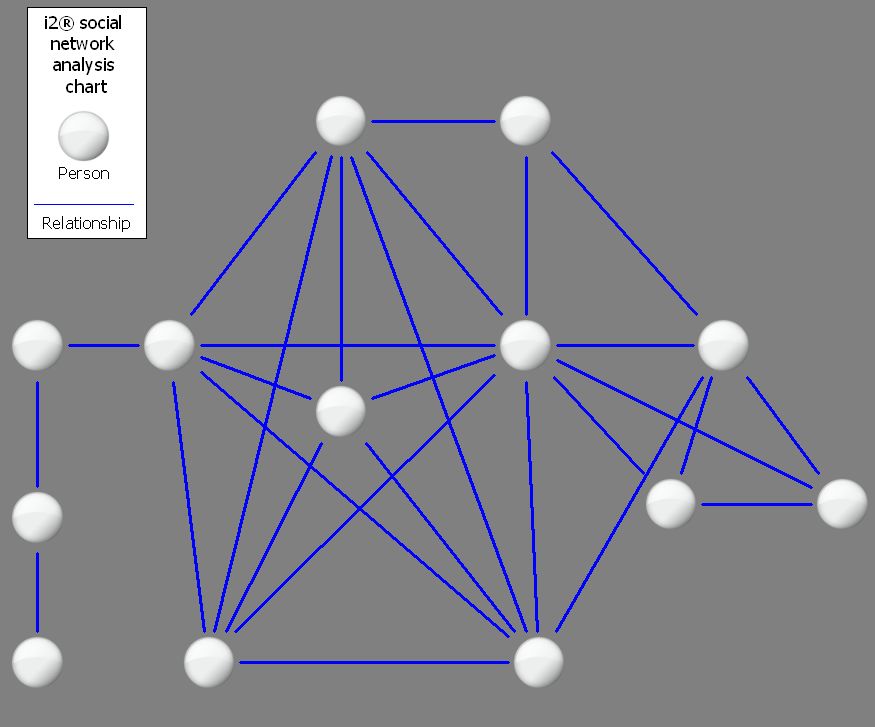
Neither should enforcement be content with arresting a courier or a trader and saying “job done”. Think about a criminal network, or some of the actors in our film. In the first picture, each person is a white bubble and their associations with each other are the blue links. Fair enough; but it doesn’t tell us much more than that. So, instead of going in blind and arresting the visible (and therefore probably superficial) members of the network, ensure your investigation is tailor-made for the appropriate target.
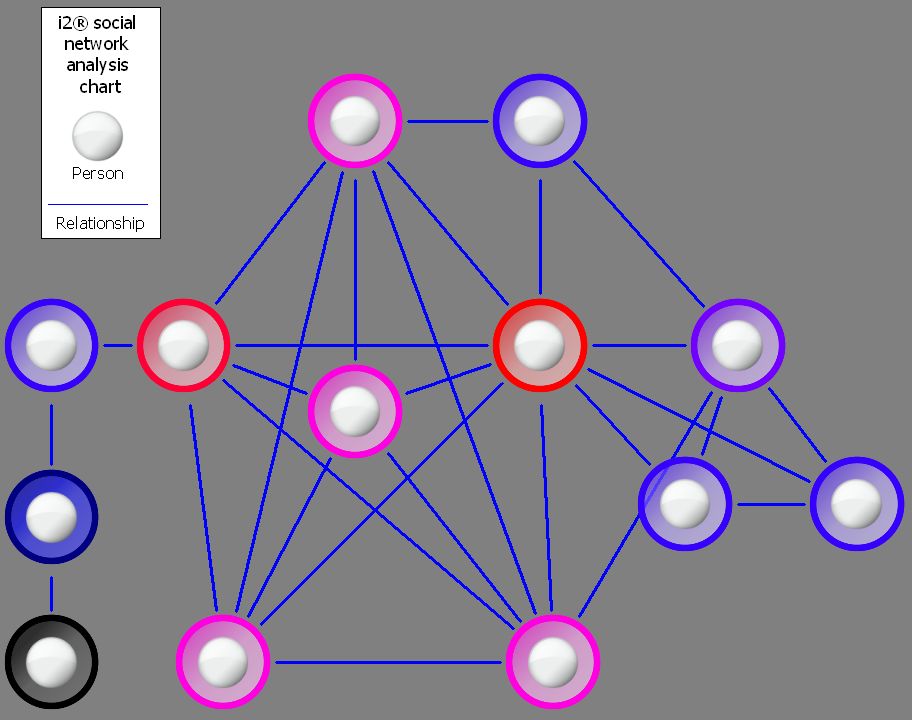
Result A
Maybe you need to target the people who control the flow of information into a network. These people are the “gatekeepers”; in Result A, they are bubbles flagged in red and then in pink (and so on in decreasingly darker shading, until those people with the least control over information). This can include people who can block those on the periphery communicating with more centrally placed individuals.
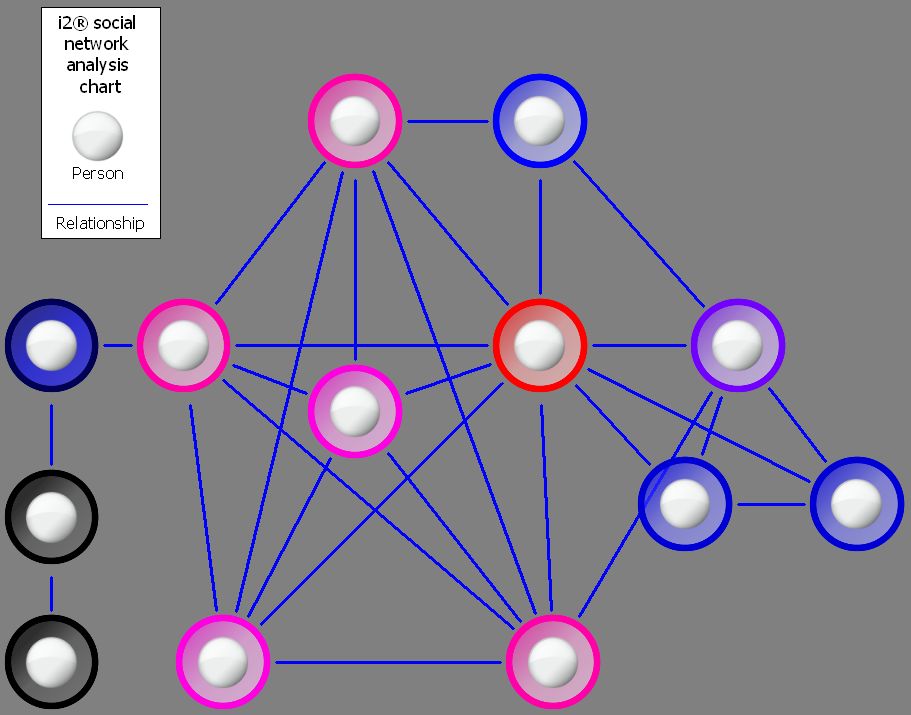
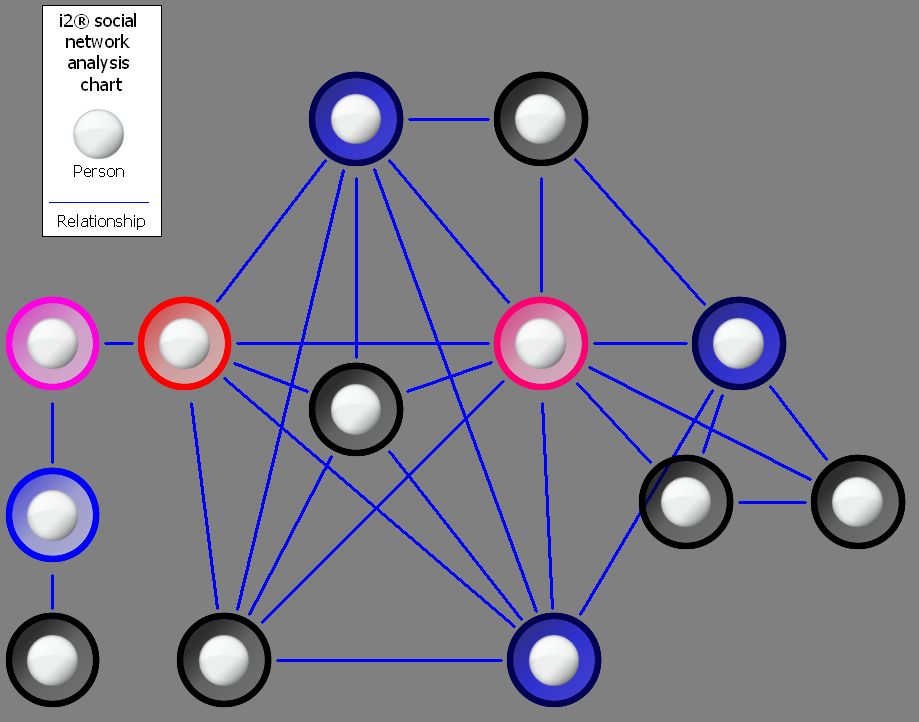
If however, you want to identify the people who have the best access to other parts of the network, then you get a slightly different result (Result B). Or, if you want to identify the people who have the strongest links within the network due to their links with well-connected people (these are “people who know people” and likely extremely influential), then it’s Result C, which is different again.
So where do you want to make the biggest impact? Do you want to disrupt, fragment or shatter the network? Identifying the different roles in a network provides subtly different options for developing an investigation, and a way of maximising limited resources. It enables the targeting of those players whose removal will most effectively halt criminal activity.
Yes, networks will no doubt be more complicated than this example, and they can be loose and fluid, and not always easy to identify. But that’s where commitment and an intelligence-led approach comes in. And now world leaders have now made a commitment to protect wild tigers – let’s have a screenplay with a difference. Who wins the award for best enforcement? Who’s writing the script anyway?
Reference 1CITES Secretariat, Report by the CITES Secretariat on its verification and assessment mission to China, 28 March-7 April 2007, CoP14 Doc. 52 Annex 7 (2007)